At Proton, we’re always working on new and innovative ways to protect the privacy and data of the Proton community. Sometimes that means developing entirely new services, like our Proton Sentinel program, which combines AI and human security analysts to increase the account security for high-profile users. Other times, it means taking an old idea and putting a new twist on it, like our new, custom-built CAPTCHA.
In our What are CAPTCHAs? post, we introduced what CAPTCHAs are, how they work, and a roadmap for future development to keep CAPTCHAs ahead of the game as a first line of defense against bots and spammers on the internet.
At Proton, we also need to defend our website against bots and spammers. However, as we investigated available CAPTCHA options, we weren’t satisfied, so we decided to develop our own. Our primary goal was to provide a system that doesn’t compromise on privacy, usability and accessibility, or security. If you plotted those three priorities on a chart, we wanted our CAPTCHA to be firmly in the center.
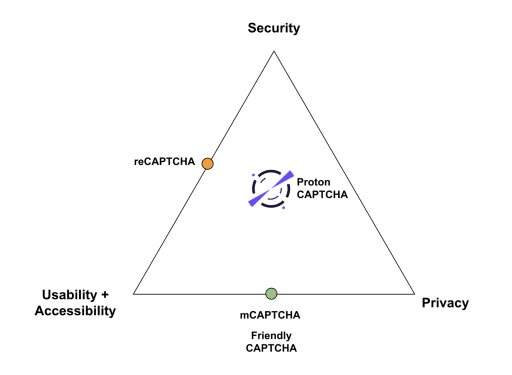
Moreover, building our own solution meant that we could resolve current CAPTCHA availability issues for members of the Proton community in countries with restricted internet issues (for example, Iran and Russia). Because of our unique needs, Proton CAPTCHA is the world’s first CAPTCHA with censorship resistant technologies built-in.
Our system offers the following features:
- Built with a privacy-first approach that’s fully GDPR compliant
- Mobile friendly
- No third-party services
- Support for alternative routing, allowing access to those in restricted countries
- Multiple defenses:
- Proof of work: Computational challenges with adjustable difficulty.
- Visual challenges: Multiple visual challenges, including our CERN-inspired particle collision challenge.
- Privacy-preserving bot detection
- Support for the visually impaired
Proton CAPTCHA’s differentiator comes in its multi-layered defense strategy, combining visual challenges with computational proof of work. Why both? While computational proof of work makes it more “costly” for attackers to hit a website, it doesn’t stop them from doing so. Visual challenges, however, are still effective at stopping the majority of attacks.
A multi-layered defense strategy

Combining visual challenges with computational proof of work (PoW) in CAPTCHA systems creates a multi-layered barrier that offers the following benefits:
- Defense in depth: Combining two different types of challenges provides a “defense in depth” strategy. Even if one layer is compromised, the other layer still provides a level of security.
- Adaptive difficulty: The difficulty of the computational task can be adjusted based on suspicious behavior. For instance, if a user fails a visual CAPTCHA several times, the subsequent PoW can be made more challenging, slowing down potential bots.
- Enhanced accessibility: For users with visual impairments who find traditional CAPTCHAs difficult, computational proof of works offers an alternative way to verify themselves while still providing a layer of protection against bots.
Proof of work
Initializing a CAPTCHA can itself be a heavy server process since there is a requirement to generate the visual challenge involving image processing. To protect against attacks on even this endpoint, we also add proof of work as a line of defense to dissuade bots that try to use our own CAPTCHA system against us.
Proof of work in general is becoming more popular with mCaptcha(new window) and Friendly Captcha(new window) emerging in this space. However, reliance on computational challenges as your only defense strategy is risky. While these challenges are unintrusive, they heavily depend on the user’s device and its abilities (processor speed or memory). If a device is too slow, the user experience can be suboptimal, as you may have to wait many seconds for the challenges to complete. On the other hand, powerful servers used by a spammer would have no difficulty solving these challenges relatively quickly.
To address this, we conducted extensive tests on a variety of devices internally while developing our system. This helped us calibrate appropriate difficulty settings for all device types. If our CAPTCHA observes a high number of failures on the visual challenges, it’s designed to increase the difficulty level of the proof of work challenge accordingly.
In this manner, a botnet that can bypass the initial proof of work but struggles with the visual challenges will be met with increasingly complex computations. This escalating difficulty makes the process more costly for the botnet but normal people will be able to pass quickly.
Visual Challenges
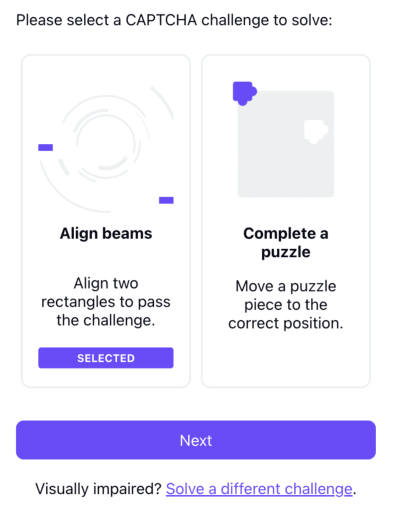
The typical CAPTCHA is a visual challenge (or audio challenge for the visually impaired). With Proton CAPTCHA, we built a modular system that supports multiple challenge types. We have set out to make the CAPTCHA at least a bit more fun than traditional CAPTCHAs and have even created our own CERN-flavored game. At present, we have two:
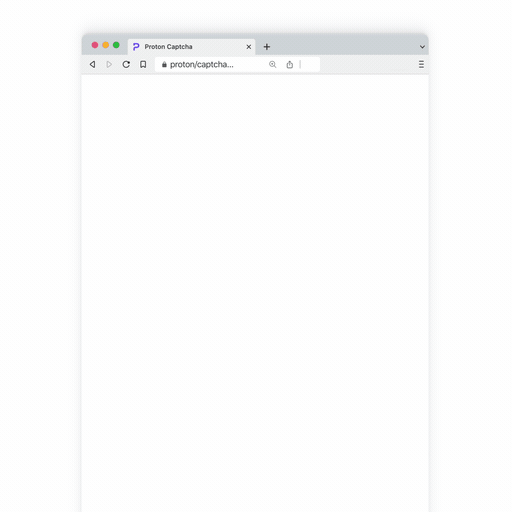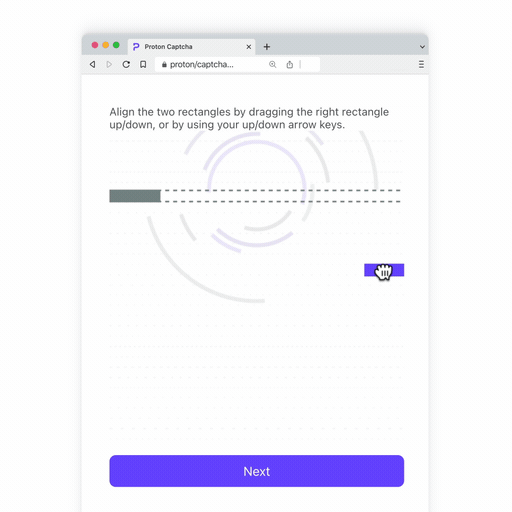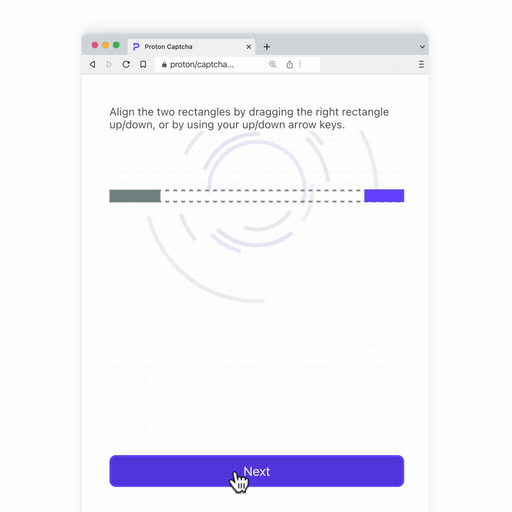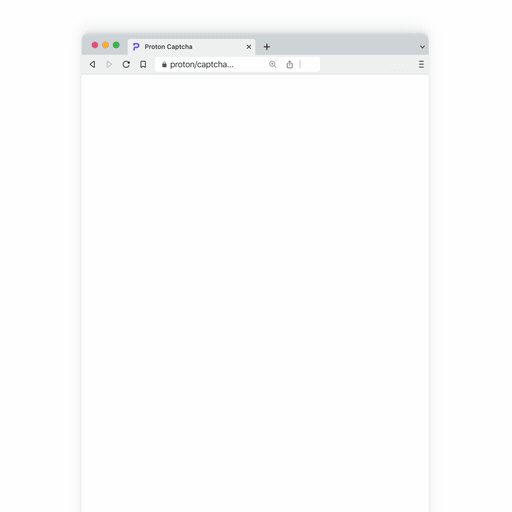
- A beam alignment challenge: Inspired by our particle colliding origins at CERN(new window), the goal is to align two rectangles that represent a beam line (where the particles are fired from) so they can collide. The animation at the end is worth the effort, we promise.
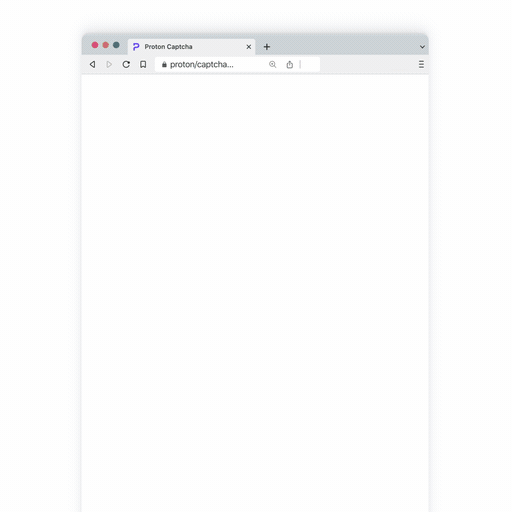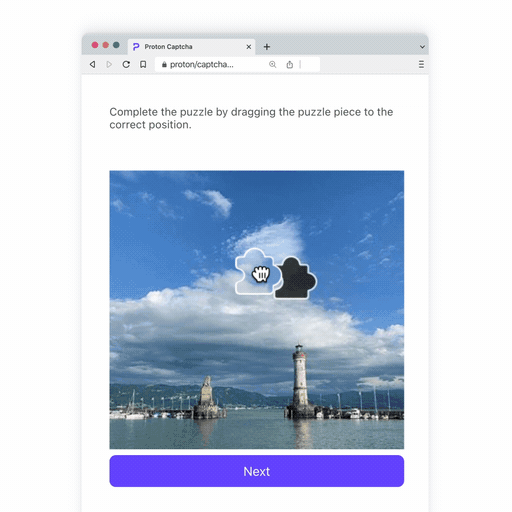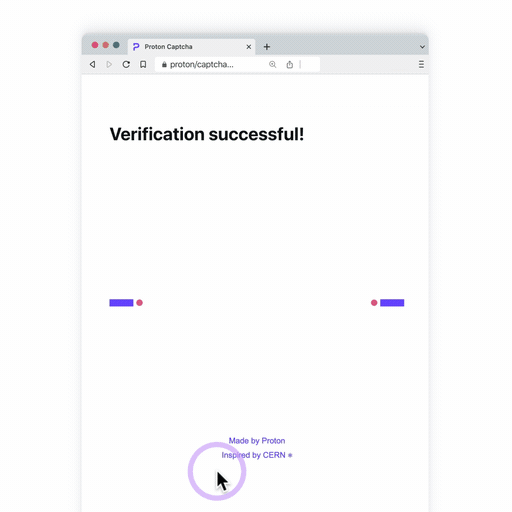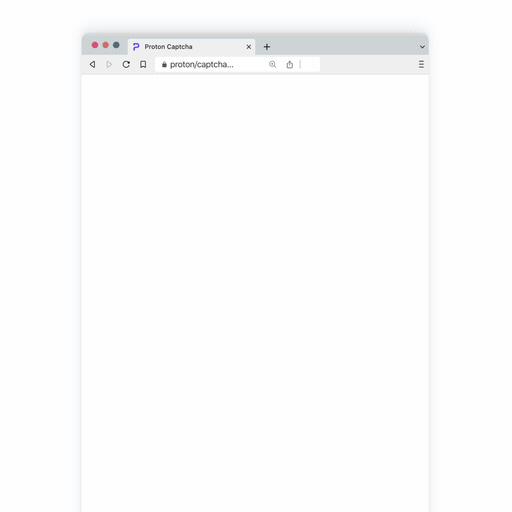
- An intuitive 2D puzzle: Our puzzles are constructed dynamically on the server using many base photographs, some from Proton employees, the rest from Unsplash(new window). This means it’s unlikely you will see the same puzzle twice.
Summary
Proton CAPTCHA has already been served to millions of users over the past months, with 100% of sign-up and login CAPTCHAs now using our in-house solution.
However, this is only the start of the journey. Our goal is to provide a CAPTCHA that is accessible, usable, privacy-preserving, and secure against even the most advanced threats. As such, you can expect to see more innovation in this space, with the goal being to reduce the burden of CAPTCHA for real users while making it hard for attackers to abuse our services.
We look forward to hearing your feedback and suggestions! In the future, we may also consider making it available for third-parties who care about privacy via an API. To find out more, you can contact us at [email protected].





