Encryption explained
Encryption is the key to security on the internet. It keeps your personal information private and secure by scrambling it into what appears to be random text. Read on to learn more about encryption, why it matters, and how Proton uses encryption to protect your digital life.

What is encryption?
Encryption is the mathematical process of transforming information into an unreadable code, so that no one can decipher it unless they have the correct cryptographic key. Without encryption, anyone could intercept, read, or alter your sensitive data, including photos, passwords, and messages.

What does encryption mean?
Put simply, it means your data is unreadable without the correct key. It keeps your information safe from prying eyes.
How does encryption work?
The most common way to encrypt information is to transform the readable text, known as plaintext, into unreadable text, called ciphertext, using mathematical operations known as algorithms. These algorithms use a cryptographic key, or a set of shared mathematical values (like prime numbers or elliptic curves), to scramble a file. Only the matching key can decipher the file and convert it back into its original format.
To someone without the correct cryptographic key, an encrypted file looks like random data, but encryption follows logical, predictable rules. It has to, because otherwise, decryption would be impossible.
The security of an encryption algorithm depends on its complexity. Modern encryption uses complex algorithms and strong key sizes so that even the strongest supercomputers cannot guess every possible answer in a reasonable amount of time.
Data is typically encrypted when it’s stored (“at rest”) and when it’s sent between devices (“in transit”).

Encryption example
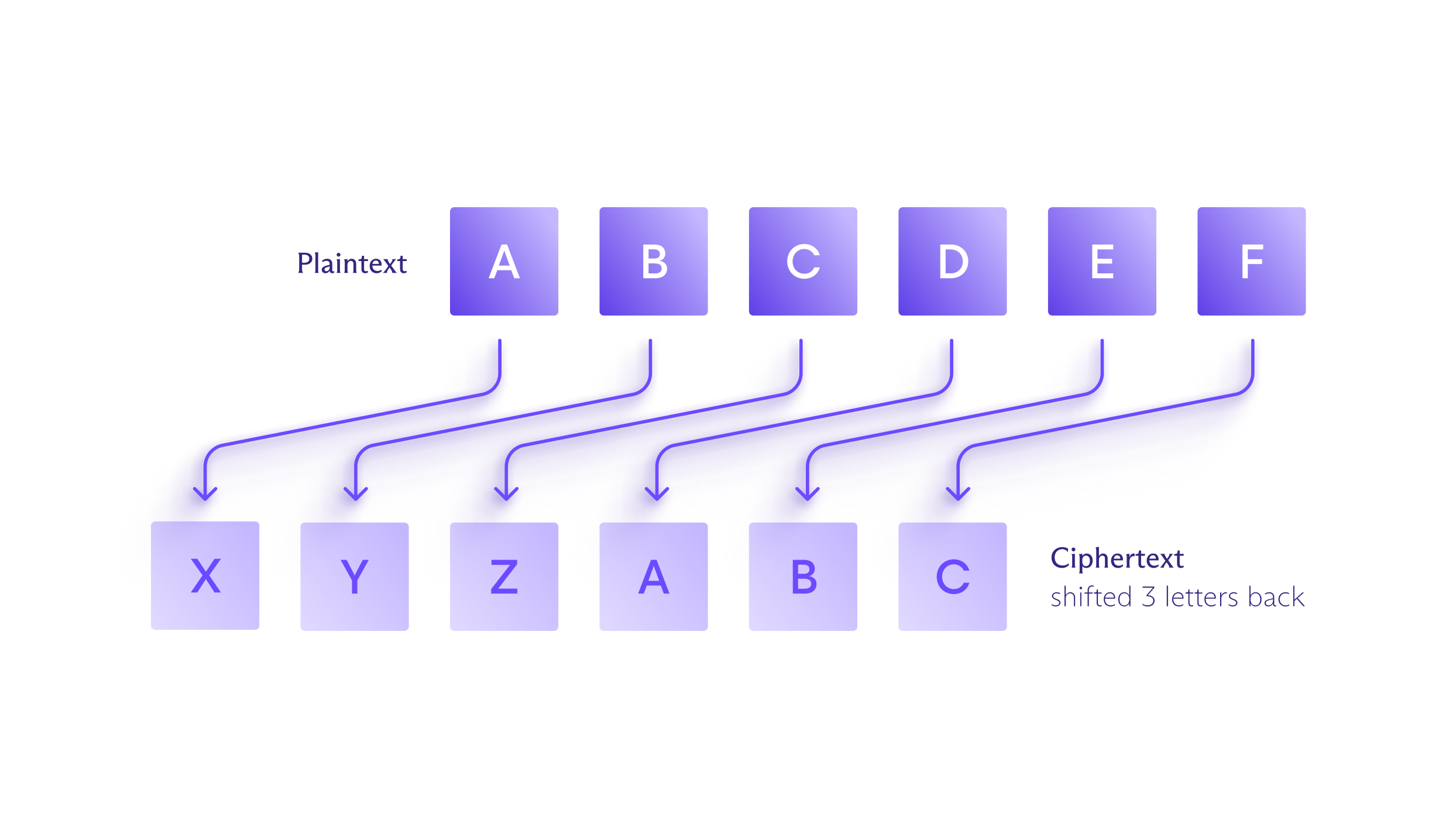
One of the best-known examples of encryption is the Caesar cipher, used by Julius Caesar to keep his messages private. In this cipher, each letter in the original text is replaced by another letter moved up or down a fixed number of positions in the alphabet. For instance, by shifting three positions backwards, “A” becomes “X” in the ciphertext, “B” becomes “Y”, and so on.
Of course, ciphers (a specific algorithm used for encryption) have since evolved to become far more complex, making them much harder to crack. Modern encryption is handled by complicated algorithms that can encrypt plaintext and then decrypt ciphertext in milliseconds, so you don’t have to sacrifice convenience for security.
Types of encryption
Broadly speaking, encryption comes in two types: symmetric and asymmetric. Each has strengths and weaknesses.
Symmetric encryption
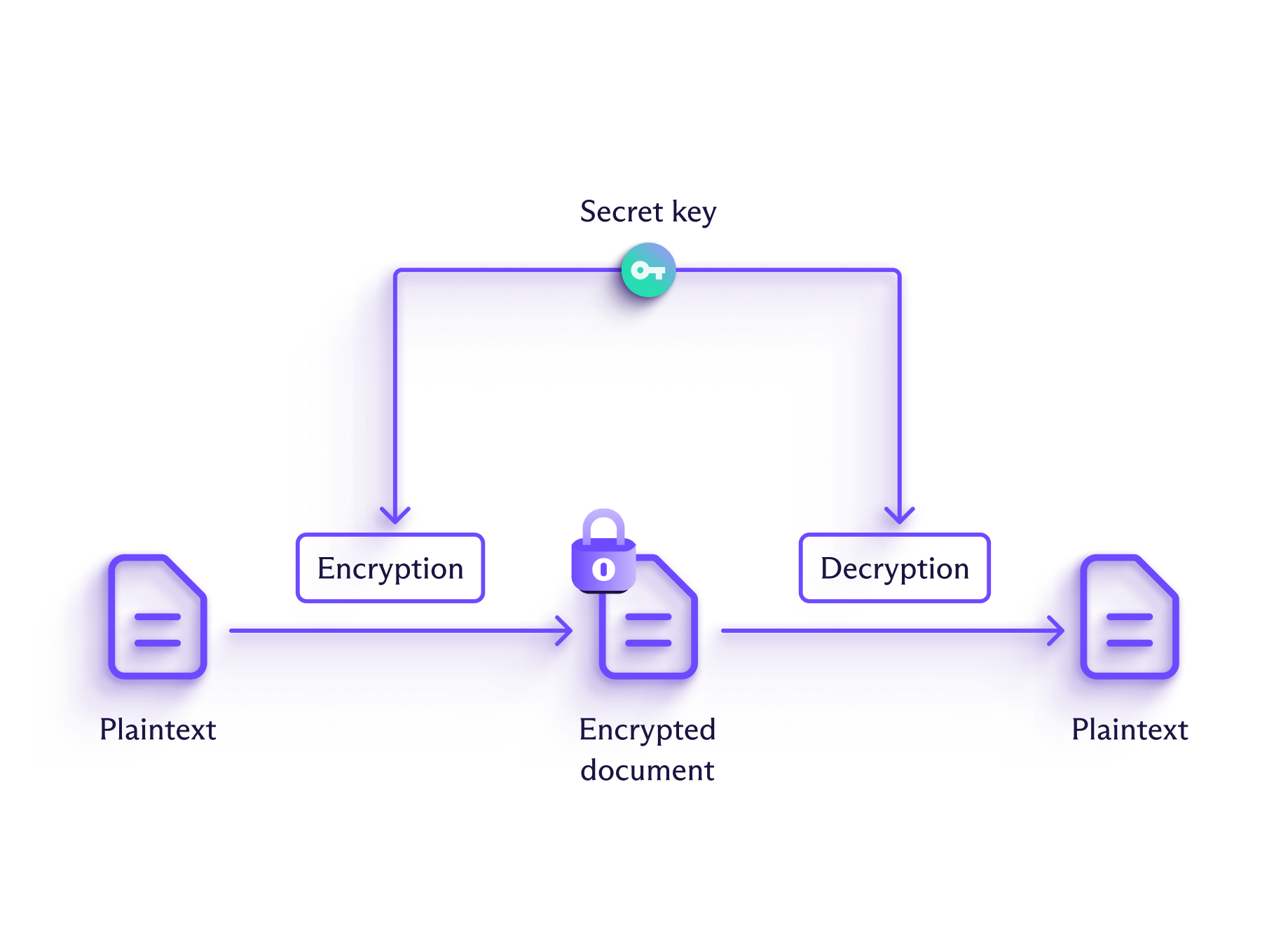
In symmetric encryption, the same key is used to encrypt the plaintext and decrypt the ciphertext. The Caesar cipher is a historical example of symmetric encryption.
Symmetric encryption is much faster than asymmetric encryption, but it has a big drawback: If an attacker intercepts both the key and the message, they’ll be able to read its contents. To protect the key during transmission, symmetric cryptographic keys are often themselves encrypted using asymmetric encryption.
Asymmetric encryption
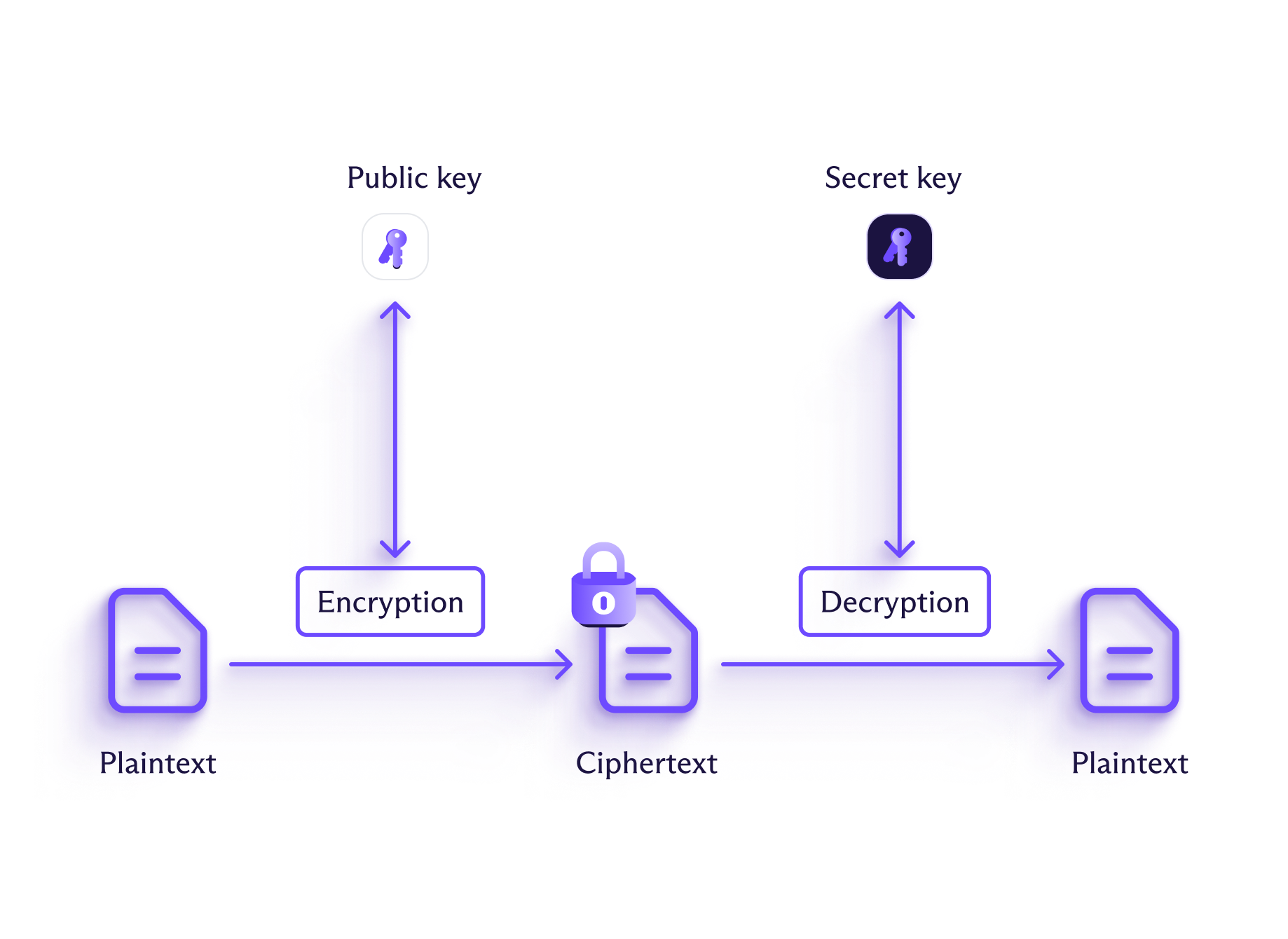
With asymmetric encryption, different keys are used to encrypt and decrypt the information. These keys are paired: The sender uses a public key to encrypt information, and the recipient uses a private one to decrypt it. Anyone can use the public key to encrypt information (which is why this is also known as public-key encryption), but only the person holding the corresponding private key will be able to decrypt it.
Think of it like having a mail slot in your door: Anybody can throw letters in, but you need a special key to open the mailbox and read them. This allows anyone to send you a message without exchanging a secret key in advance.
In comparison with symmetric encryption, asymmetric encryption is generally considered more secure as it eliminates the difficulty of securely sharing the encryption key. However, it also tends to be a lot slower, making it a less desirable option for encrypting larger amounts of data.
What are encryption algorithms?
When you use a service that encrypts data, the encryption is handled by algorithms, which are complicated mathematical formulas. The two main categories are symmetric and asymmetric algorithms.
An encryption key’s security is tied to its length, which is measured in bits. The difficulty of cracking a key grows exponentially as its length increases.
For example, a 1-bit key has only two possible values (1 or 0), making it easy to guess. A 128-bit key, however, would have a 340 undecillion possible combinations (that’s 340 with 36 zeros behind it), making brute-force attacks virtually impossible.
Generally, symmetric encryption keys of 256 bits are seen as secure, but asymmetric keys must sometimes be thousands of bits long to provide similar levels of security.
Symmetric encryption algorithms
Symmetric algorithms usually encrypt information either bit by bit (called stream ciphers) or in blocks of several bytes (called block ciphers).
The main upside of using symmetric encryption is that it’s fast, making it a good choice for things like full-disk encryption or VPN traffic.
Examples of symmetric encryption algorithms are AES (Advanced Encryption Standard) and ChaCha20.
Asymmetric encryption algorithms
Asymmetric encryption is slower than symmetric encryption because of the mathematics it must perform to encrypt and decrypt ciphertext. Though the delay can be measured in milliseconds, this adds up when dealing with large files.
This means asymmetric encryption is most commonly used to handle key exchanges, not bulk data encryption. A symmetric encryption key is generally used to encrypt the data, and then asymmetric encryption (like encrypting it with the recipient's public key) is applied so it can be securely transported across open networks like the internet.
Common asymmetric encryption algorithms include the RSA (Rivest–Shamir–Adleman) cryptosystem and ECDH (Elliptic-curve Diffie–Hellman), which is used to securely agree on encryption keys.
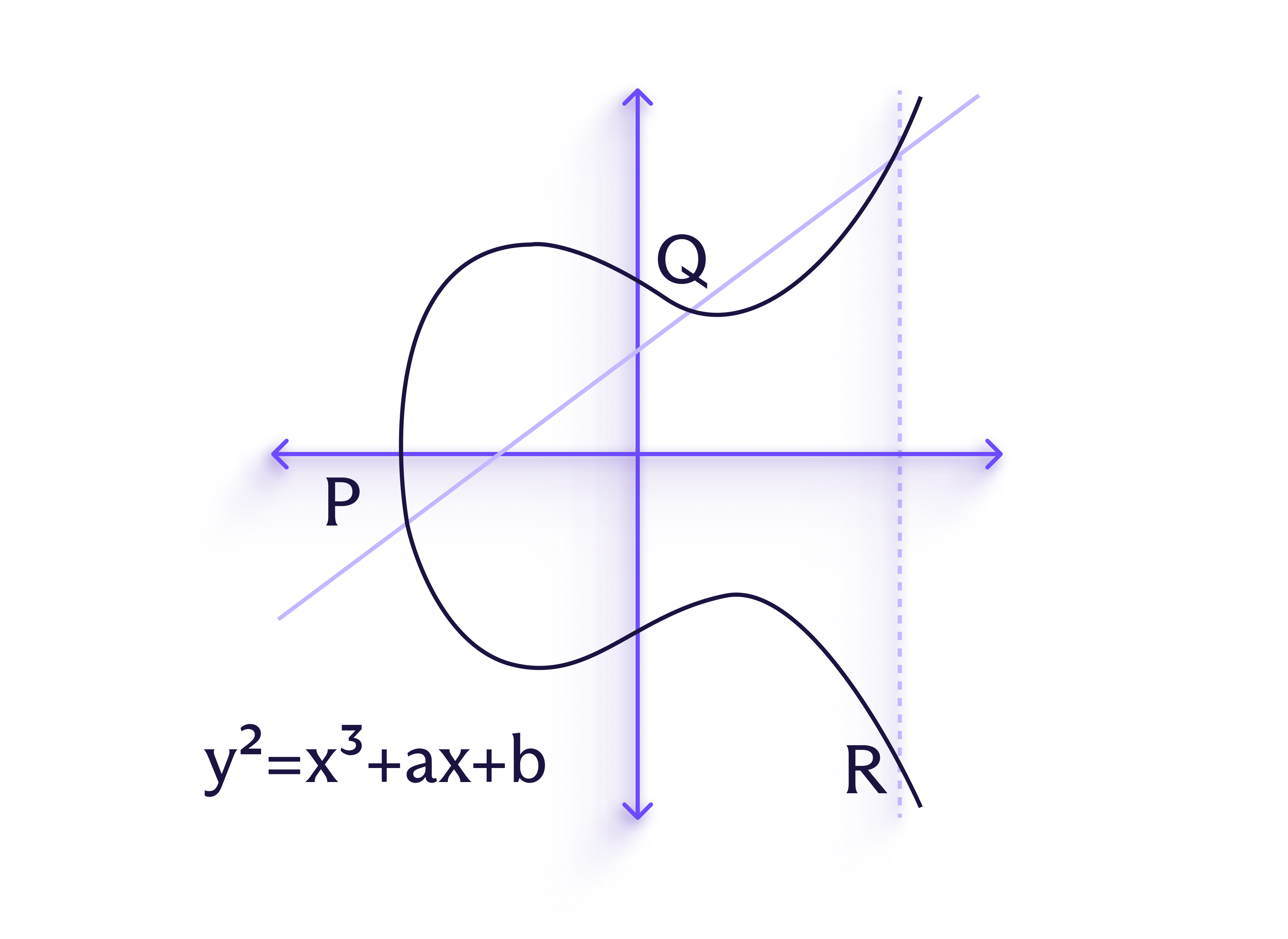
ECDH is a specific type of elliptic-curve cryptography (ECC). ECC relies on the structure of elliptic curves (pictured) to achieve greater security without requiring longer keys, making it useful for applications where resources are limited, such as messaging.
Symmetric vs. asymmetric encryption: Differences
Symmetric encryption | Symmetric encryption | Asymmetric encryption |
|---|---|---|
Method | Uses a single key for both encryption and decryption | Uses two different keys — one public key to encrypt and one private key to decrypt |
Speed | Fast | Slow |
Key length | Usually 128-256 bits | Usually ≥2048 bits for RSA, ≥256 bits for ECC |
Common uses | Protecting large-sized data, such as local systems and databases | Securing messages and other communications |
Examples | AES, ChaCha20 | RSA, ECDH |
Why is encryption important?
The main benefit of encryption is to make sure information stays private, especially as it travels through the internet. Encryption has become much more common online, especially on messaging apps and services that handle sensitive data, like banking apps.
In fact, just about every website is now protected by TLS (indicated by “https” at the beginning of the URL). TLS uses asymmetric encryption to securely exchange a symmetric encryption key, then switches to symmetric encryption to protect your data during the session.
Strong encryption is particularly important for businesses, as powerful data protection is essential for compliance with data regulations such as HIPAA (governing health data in the US), GDPR (governing general data privacy in Europe), and PCI DSS (governing payment systems worldwide).
How does Proton use encryption?
At Proton, your privacy and security come first, which is why we design our apps to use end-to-end encryption (E2EE) and industry-leading cryptography.
Where applicable, our apps use E2EE, meaning your data is encrypted on your device and isn’t decrypted until it reaches its destination device.
Contrast this with your standard email or cloud storage service, which traditionally encrypts your message or file in transit, decrypts it upon arrival to its servers, and then re-encrypts it for storage — all using encryption keys that it controls. This is inherently less secure, as the service provider holds the keys it needs to access your messages or files at any time.
To apply E2EE, we use the OpenPGP standard, which combines the speed of symmetric encryption with the security of asymmetric encryption, similar to TLS. Additionally, OpenPGP is open source, meaning anyone can analyze it to validate and improve its security.
Each Proton service applies encryption differently, depending on how that service is used. Here’s how we use encryption to ensure you control your data:
Our mail app end-to-end encrypts emails sent from one Proton Mail user to another. E2EE can be enabled for emails from Proton Mail to non-users with the Password-protected Emails feature.
All messages in Proton Mail are stored with zero-access encryption.
With Proton VPN, all internet traffic is encrypted with either ChaCha20 or AES-256, two secure algorithms.
Additionally, Proton VPN only uses ciphers and protocols that support perfect forward secrecy; even if future VPN sessions are compromised, your past sessions stay secure.
Cloud storage has never been more secure. Thanks to our E2EE, which uses the OpenPGP standard and ECC, no one else can access your Proton Drive files without permission.
This also extends to file sharing, so you can easily share your Proton Drive photos, folders, and other assets with privacy and peace of mind.
All your usernames and passwords are encrypted with E2EE in our secure password manager.
Through 256-bit AES-GCM encryption, all stored items are kept in vaults encrypted with randomly generated 32-byte keys that cannot be brute-forced, keeping all your credentials safe.
Proton Calendar uses the OpenPGP standard and ECC to encrypt your events and contacts end-to-end. When you invite someone to an event, their information is encrypted so no one can know their identity.
Shared calendar invites are cryptographically verified so attendees can be sure it was you who invited them.
Protect yourself with Proton encryption
Now that you know how encryption works, put it to work. Protect your data with Proton.
Frequently asked questions about encryption
- Is all encryption equally secure?
- Is encryption future-proof?
- If someone steals my encryption key, can they read all my past messages?
- Do I need encryption for everyday use?
- How does encryption protect against hackers?
- Is encryption the same as a password?
- Does encryption slow down performance?
- Can I share my encrypted data with others?
- Can the government or law enforcement get access to end-to-end encrypted messages?
- Is encryption legal?